30+ cyber security network diagram
Get the most powerful professional diagram software on the market. The most Simple and Yet Powerful SIEM Solution to all Log Management and Security Needs.

Cheat Sheets Packetlife Net Computer Programming Computer Technology Computer Network
Prices and download plans.

. Ad CDW Experts Can Assess Your Cybersecurity Practices and Recommend Improvements. The Network Security Diagrams solution enhances the ConceptDraw PRO v10 functionality with large collection of predesigned vector stencils of cybersecurity clipart shapes icons and. Creately diagrams can be exported and added to Word PPT powerpoint Excel Visio or any other document.
Ad Complete your network diagram in minutes with automated network mapping from Auvik. The network diagrams used throughout this book have also been intentionally. Sign in Sign up for FREE Prices and download plans.
Ad Save Time Ensure Compliance With Automated Network Configuration Management Backup. Ad Real time Security Information Event and Management software. Import Modify Visio.
Find the Best Network Security Systems That Will Help You Do What You Do Better. At UKDataSecure we have the knowledge and experience required to support you in reviewing and updating your current network and data flow diagrams to support your. Supplement an institutions understanding of information flow within and between network segments as well as across the institutions.
Free trial up and running on your network in 30 minutes or less. Ad Includes Networking Cisco LAN Rack Diagrams. A Data Flow Diagram should.
Ad Easily Find The Network Security Systems Youre Looking For w Our Comparison Grid. Ad Lucidcharts network diagram software is quick easy to use. Knapp Raj Samani in Applied Cyber Security and the Smart Grid 2013 Diagrams and Figures.
Learn how IT infrastructure monitoring ITIM tools help tackle monitoring challenges. Ad Complete your network diagram in minutes with automated network mapping from Auvik. You can edit this template and create your own diagram.
Free trial up and running on your network in 30 minutes or less. Ad Read why organizations adapt to hybrid modular dynamic and cloud-based environments. Work with Us to Develop Cohesive Strategies and Make Your Data More Secure.
Use PDF export for. Resolve Operational Issues Faster By Easily Identifying Troubleshooting Problems.

How To Use The Nist Cybersecurity Framework 5 Minute Guide For Enterprise Security Architects Youtube

Private Networks Nextgen

7 Cybersecurity Career Paths Jobs To Consider In 2022

4g To 5g Evolution In Depth Security Perspective Youtube

Access Programmer Consultants Access Database Relationship Diagram Database Design

Secure And Intelligent Slice Resource Allocation In Vehicles Assisted Cyber Physical Systems Sciencedirect

Of Cybersecurity Passwords And Staying Safe Online Via Http Wpengine Com Unmasked Football 24 Cyber Security Abc 123

Access Programmer Consultants Access Database Relationship Diagram Database Design

Intex It Intex It Twitter

These Are The 5 Stages Of Growth Hacking Funnel That You Must Pass To Grow Your Business Entrepreneurship Sta Growth Marketing Growth Hacking Growth Medium

What Is Network Security Introduction To Network Security Network Security Tutorial Simplilearn Youtube

Cyber Security Incident Response Cheat Sheet Behavior Analysis Cyber Security Analysis
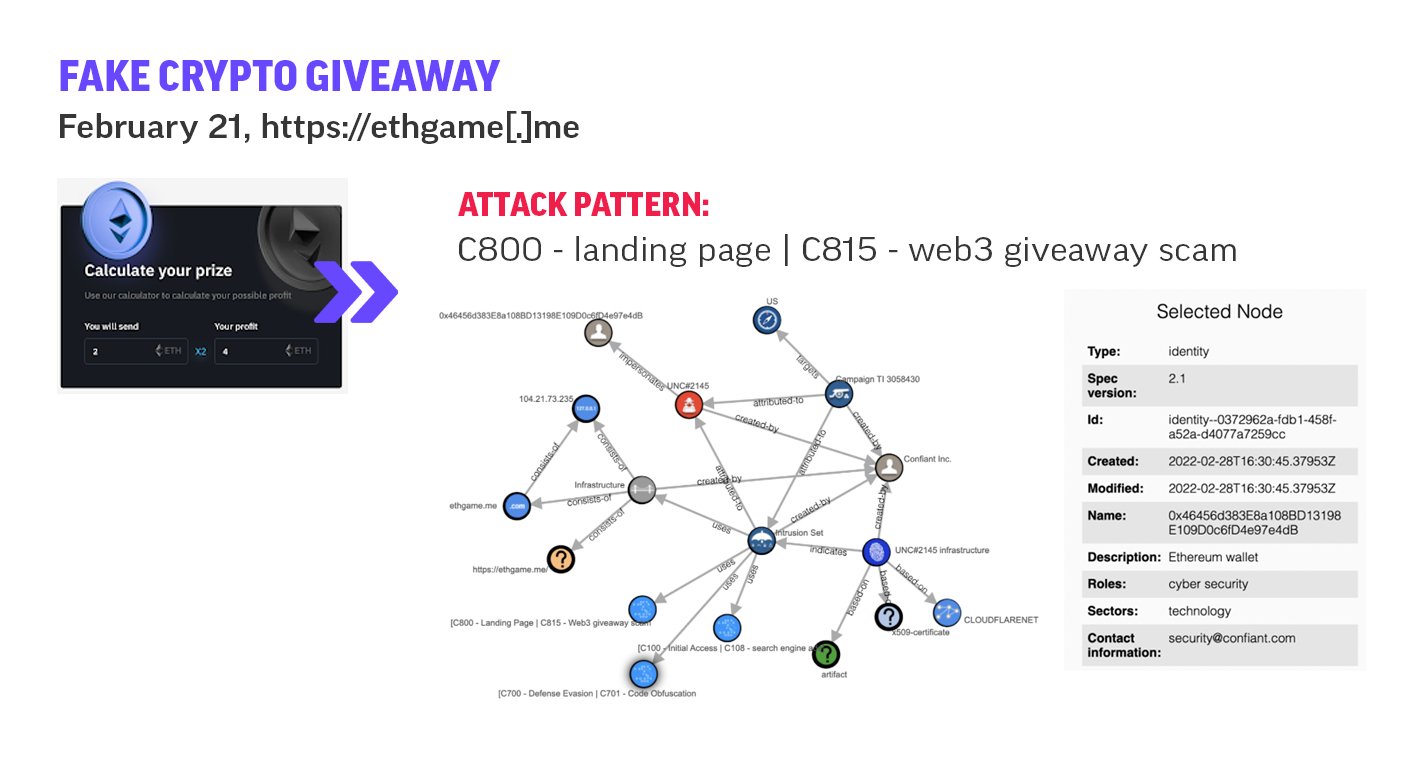
Enterprise Security

Cybersecurity Companies Start Ups To Watch In 2021
Cybersecurity Companies Start Ups To Watch In 2021

30 Data Breach Statistics And Facts Frequency Impact More

Seo Marketing Hub A Free Library Of Seo Resources Searchengineoptimization Digitalmarketing Seotips Seo Marketing Seo Software Marketing